
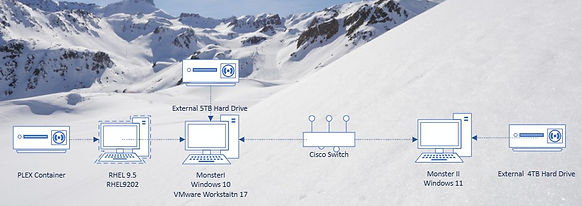
PLEX Container
Deploying Plex Media Server in a Podman container on RHEL 9.5 provides a secure and efficient way to manage your media server without installing additional software directly on the host.
Benefits of Running Plex in a Container
✅ Isolation & Security – Runs separately from the host system, reducing risks.
✅ Portability – Easily move or back up your Plex setup.
✅ Automatic Updates – Keep your media server up-to-date with minimal effort.
✅ Less System Overhead – No need for additional system dependencies.
By running Plex in a rootless Podman container, users ensure better security while maintaining full functionality. The setup involves mapping storage volumes for configuration, media, and transcoding, while allowing network access to Plex’s streaming services.
RHEL PLEX Media Server Container Setup
Informational
-
PLEX server was running on Windows 10 but that system died
-
PLEX media on external 4TB hard drvie WD Passport formatted with NTFS
-
Currently connected to new gaming system called MonsterII
Firewall Rules
sudo firewall-cmd --permanent --add-port=32400/tcp # Plex Web UI and Streaming
sudo firewall-cmd --permanent --add-port=3005/tcp # Plex Companion
sudo firewall-cmd --permanent --add-port=5353/udp # Bonjour/Avahi for Network Discovery
sudo firewall-cmd --permanent --add-port=8324/tcp # Plex Roku Remote
sudo firewall-cmd --permanent --add-port=32410/udp # GDM Network Discovery
sudo firewall-cmd --permanent --add-port=32412/udp # GDM Network Discovery
sudo firewall-cmd --permanent --add-port=32413/udp # GDM Network Discovery
sudo firewall-cmd --permanent --add-port=32414/udp # GDM Network Discovery
sudo firewall-cmd --reload
Container Setup
Login to Registry:
podman login registry.redhat.io
Pull Image to Local System:
podman pull docker.io/linuxserver/plex:latest
SELinux Options
Check Status: getenforce
If this is set to enforcing like mine was it was stopping Plex
from accessing my mounted dive paths.
Option 1) Disable SeLinux Temporary (Verified)
sudo setenforce 0 # disable
Option 2) Adjust the Context so can run with SeLinux enabled (Verifed). The chcon command changes the security context of files and directories in Linux. It's short for "change context" or "change security context.
In Linux, the label container_file_t is used to label all content within a container. This label is used in conjunction with the container_t label, which is used to label the container process itself.
Config Folder Labeling:
sudo chcon -R -t container_file_t /mnt/container/plex/config
sudo restorecon -Rv /mnt/container/plex/config
Media Folder Labeling:
sudo chcon -R -t container_file_t /mnt/container/plex/media
sudo semanage fcontext -a -t container_file_t "/mnt/container/plex/media(/.*)?"
sudo restorecon -Rv /mnt/container/plex/media
podman stop plex
podman start plex
Wrapping up...
URL Access: Use http and then the IP address of the host RHEL server on port 32400. Just add :32400 after the IP.
Create Free Login: https://www.plex.tv/



