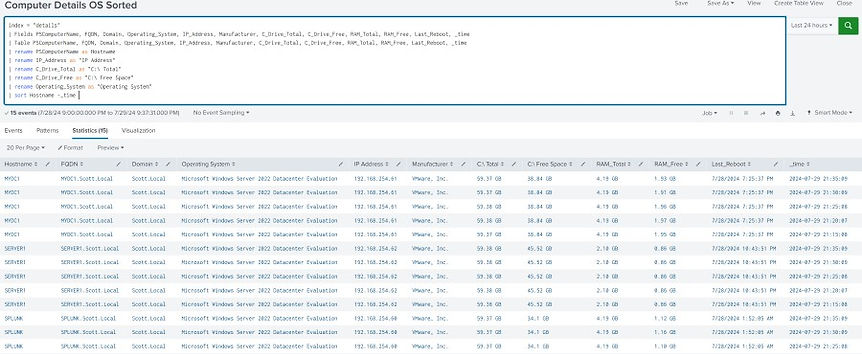
Indexes
Create Index
Creating an Index in Splunkd is like creating a subset of your data. This creates a new data set for your input instead of allowing everything to flow into the default main index. This also allows searhcing by the index name. Indexing can be done for a few different reasons; reducing size of other db for example separatng data types (servers vs networking) or simply being able to assign permissions to specific indexes.
How to create indexes ? just keep scrolling

Query Index
To query / search by a specific Index is probably the first step you learn in searching. The default index is called “main”. If you assign your data to a new index you want to change the start of you search to: index="MyIndex" using the double quotes. Be aware that searching in Splunkd is case sensitive.
Assign Index
I started out with my own battle using indexes in a standalone setup, without a Domain. I used a Universal Forwarder and all my data was going to the default "main" index. I wanted to assign it to my new index I created called “windows”.
After searching and editing a lot of .conf files that led to me starting all over again and rebuilding my entire Splunkd lab. I found out all I needed to do was change the default setting on the inputs.conf file on the Universal Forwarder on the client server sending input to Splunkd. I am posting this because I could not find anything on the web with this information or I was just too much of a noob to know what to search for.
Special Note: Says not to edit this file but I do, not sure exectly whats correct so please make sure if you are in a production setting to verfiy where to edit.
Path:
C:\Program Files\SplunkUniversalForwarder\etc\system\default\inputs.conf
Default Settings:
index = default
New Settings:
index = windows

Index Location
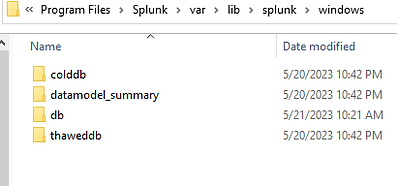
When you create a new index, you can assign a path to your new db files, or you can let it assign it dynamically. I suggest lettings Splunkd do the work for you. When creating my index called "windows" with the default parameters on my Windows system Splunkd created:
C:\Program Files\Splunk\var\lib\splunk\windows
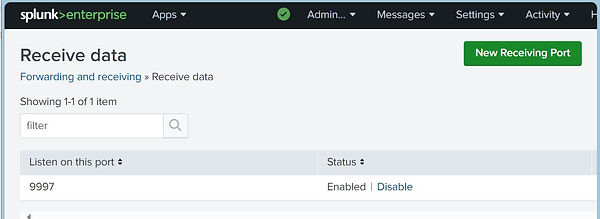
To allow inboud data to Splunk from the universal forwarder configure the default port under Forwarding and Receiving \ Configure receiving.

CREATE A INDEX
Step 1)
Navigate to the Indexes section by selecting the Settings from the top menu in Splunkd and then clicking on the Indexes menu item under data.

Step 2)
Simply click on the button in the top right called "New Index"

Step 3)
You can fill out the form that pops up and insert the new Index name. I suggest keeping it simple and all lower case. Scroll down and you can set the data retention to match requirements.

Assign an Index & Monitor CBS.log File
Step 1)
Create a new index called windows_update_logs using the process shown above.
Step 3)
I usually restart the Forwarders service on the client after making conf changes.
Step 2)
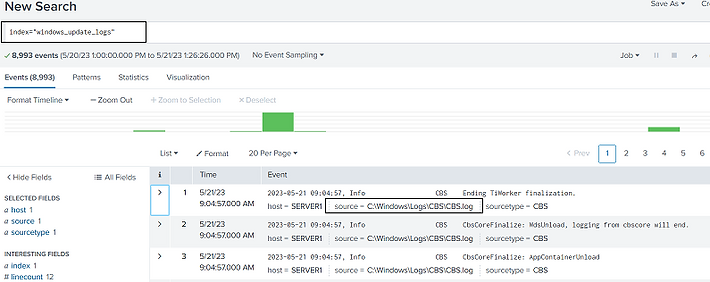
We are going to monitor a remote file that resides on a system that already has Universal Forwarder installed. There is a Windows update file called CBS.log on Windows systems that we will forward to the Splunkd server. Update the input.conf file as shown to the right with the following.
Path:
C:\Program Files\SplunkUniversalForwarder\etc\system\default\inputs.conf
Data:
[monitor://C:\Windows\Logs\CBS\CBS.log]
disabled = 0
index = windows_update_logs

Results
Now I have all my data coming from my Server1's Universal Forwarder on port 9998 that has Windows Event Viewer data stream going to index "windows" and have my Windows Update CBS log data going to index "windows_update_logs"
Note:
Universal Forwarder set to index "windows" is spoken covered earlier in site, in this page.
Asset Management using a PowerShell Script

2
Index Setup
I want Splunk to store my script results in its own index. On the Splunk server I created a index called details. This is explicitly set in the inputs.conf file on the Universal Forwarder.